Cyber Threat Monitoring System
Cyber Threat Monitoring System (CTMS) is the perfect solution to help manage the flood of information and analyze it in real-time to find evidence of security incidents. It accelerates and simplifies threat detection, incident response, and compliance management for the IT team with limited resources.
Business Benefits

Greater ROI
Allows IT personnel to uncover the full potential of the system.

Reduced risk of noncompliance.
Vairav Cyber Threat Monitoring provides the organization with CIS benchmark assessment report

Early Detection of Security incidents
Provides security analysts with a toolset that enhances their effectiveness

Broader organizational support for information security
Help break down organizational silos and create a broader and more consistent culture of security and overall risk management.

Reduced operational costs
Converging multiple tools into a single solution will enable the enterprise to save time and money
Security Capabilities
- • IT Asset Discovery
- • Host Behavioral Monitoring
- • Vulnerability Assessment
- • File Integrity Monitoring
- • CIS Control Assessment
- • Windows Security Event Monitoring
- • Network Intrusion Detection
- • Centralized Log Management
- • Host Based Intrusion Detection
- • Cyber Threat Detection
- • Security Alert and Notification
- • Rootkit Detection
- • Security Information and Event Management
- • Management Report
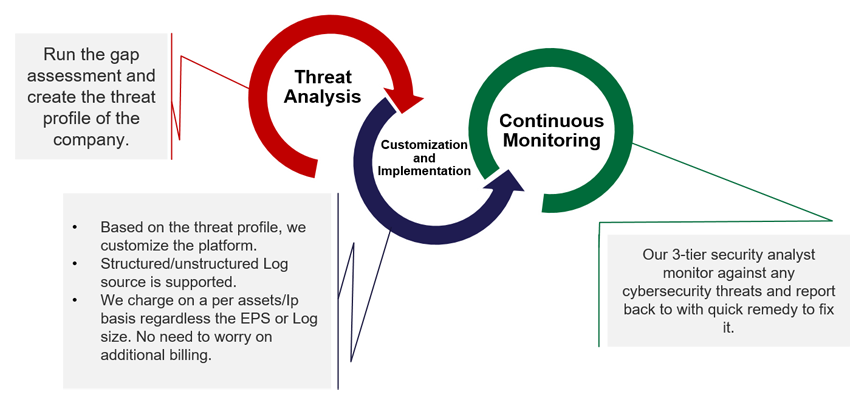
Our Approach
Hardware Required
- • Memory - 32 GB RAM
- • Central Processing Unit - 16 cores
- • Network Interface (Span port required) - 2 Network Interface 1 Gigabit Ethernet
- • Appliance Disk Storage (SSD Preferable) - 10 TB
- • Log Storage (NAS) - 4 TB
- • Virtual Machine Support